So on a test I wanted to test the possibility of performing a DoS against an IP based network camera to see of the possibility of disrupting it’s video stream. Well the idea was to hammer the device with UDP packets.
A quick look around and I found this code here. I decided to take a copy of the code as the base for a quick perl script.
A quick… Continue reading
Quiet often people ask me to bruteforce a hash for them. My usual response after the obligatory; where did you get the hash from? is “I’ll run a few dictionaries against it unless you provide me with a charset and length!”
For those that don’t understand it needs to be made clear exactly what bruteforce cracking means.
Lets just say we have a four character pin that can only… Continue reading
Today I’ve been writing my first python script. I’m using passlib.hash, unfortunately ubuntu 12.04 comes with version 1.5.3 instead of version 1.6 so there is no support for MsSQL, LM, NTLM, Domain Cached etc…
I don’t like installing packages from source as it’s a bugger to roll back if something goes wrong, so I decided to look into creating a deb package of passlib 1.6.
It’s as simple as:… Continue reading
So Linkedin hashes have recently been leaked onto the net, and plenty of people have been cracking them. Meanwhile eHarymony passwords were also leaked!
The hashes are here and a quick download is all thats needed. wget them to prevent your browser from trying to render the entire txt file!
Throwing a dictionary at it with 80,546,115 words in it results in 22% cracked passwords.
12345678910111213141516171819202122232425262728293031$ ./oclHashcat-plus64.bin eharmony.txt -r rules/best64.rule… Continue readingSo recently there has been lots of news about the linkedin password hashes being leaked which was finally confirmed on the linkedin blog.
Many of the hashes first 5 chars are obfuscated with zeros so it’s understood these are the passwords already cracked, presumably the simple ones?
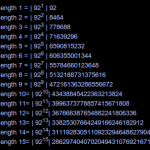
1. There are 3,521,180 hashes that begin with 00000. I believe that these represent hashes that the hackers have already broken and… Continue reading