Okay, so the first thing you’re wondering is “Why the hell would you want to do this?”
Well the answer becomes more obvious when the scenario is set: You’re on a social engineering job and you’ve managed to gain access to the target building, you walk around for a bit to see if any of the desks look free. After a while you decide to sit down at… Continue reading
So every time the BackTrack development team release a new version I download it and use it from fresh. I don’t like following the dist-upgrade route as I’ve had trouble in the past and it’s a good idea to get a clean build now and again.
I used to maintain a BT5-fixit.sh script but just don’t have the time. Instead I just use this script here: bt5r3gnome32.sh
I’ll walk through… Continue reading
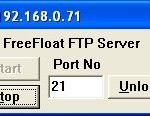
So I’ve for a while needed to learn how to exploit a service using things like NOP sleds and so on. I decided to follow this great tutorial here but wanted to make my own notes.
First off you’ll need the following:
- Windows XP x86 SP3 machine
- Immunity Debugger
- mona.py – place inside PyCommands folder of Immunity
- Freefloat FTP Server – the target we will be attacking
Background – The… Continue reading
So today I’ve been playing with python and decided to make an arp ping utility. When i get more time i’ll turn this into a simple arp scanner.
I know that this is all possible using scapy but the idea of this was to teach myself how raw sockets work within python.
This requires netifaces and a few other modules that can usually be obtained using sudo easy_install modulename (you’ll… Continue reading